In this blog post I will walkthrough of how to create a load balancer VIP to balance traffic between VMware Connection servers.
In the below case, I’ll configure an NSX edge to load balance traffic between my connection servers.
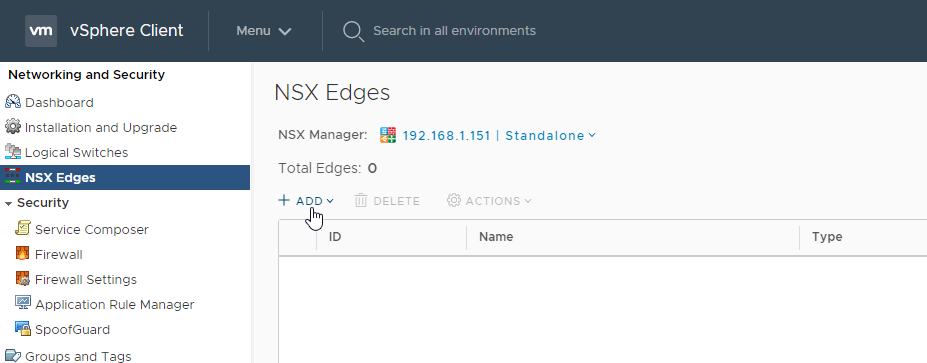
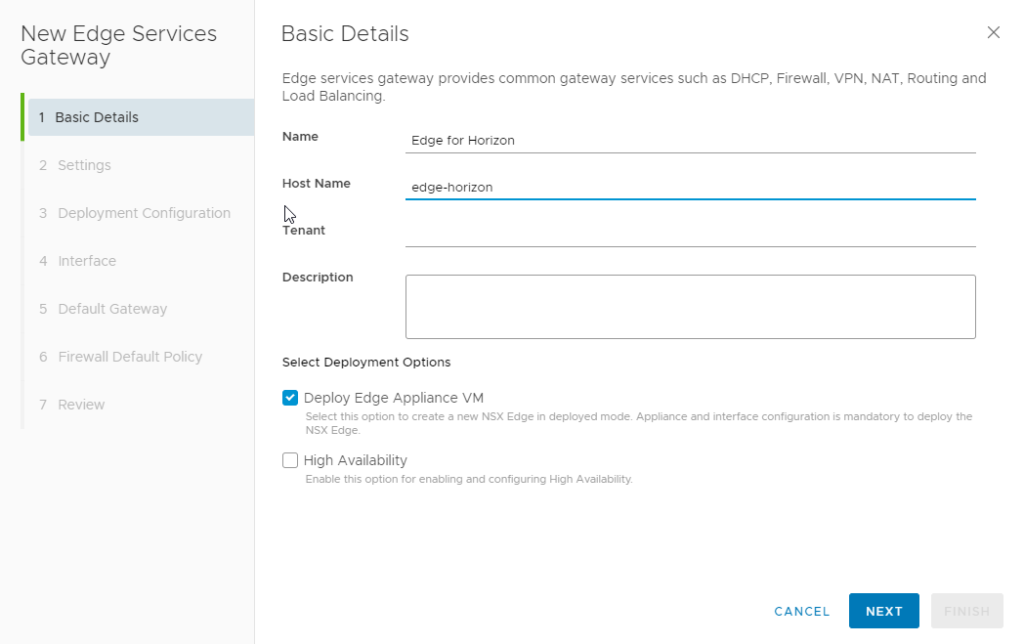
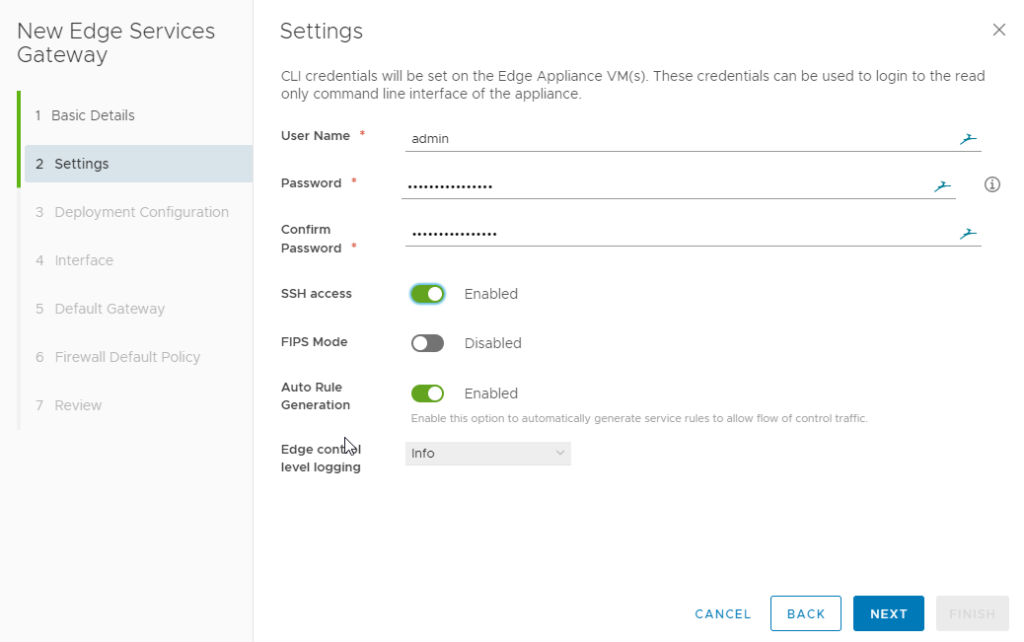
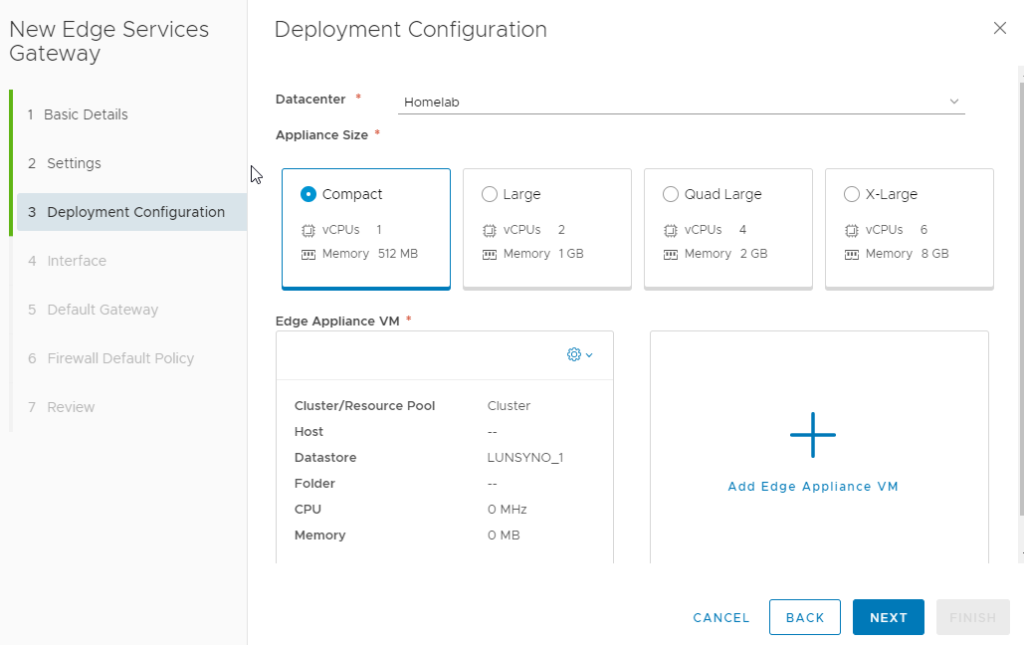
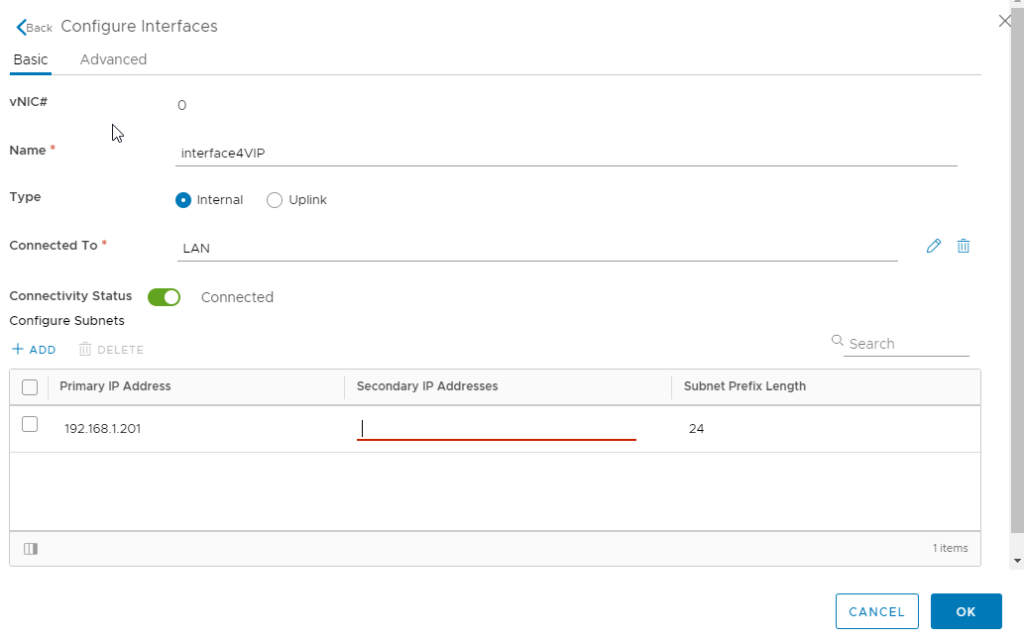
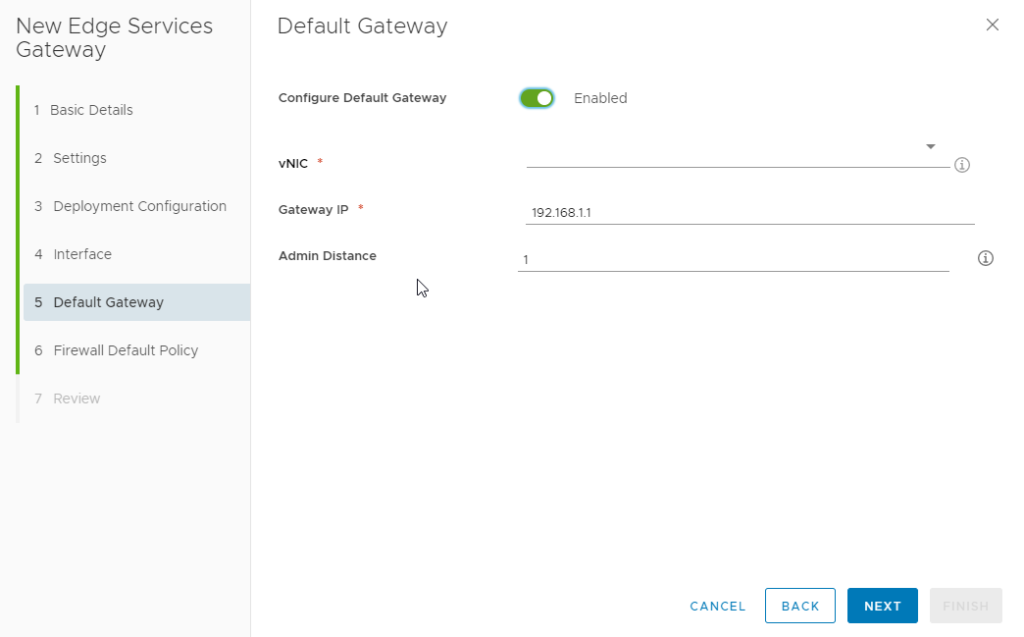
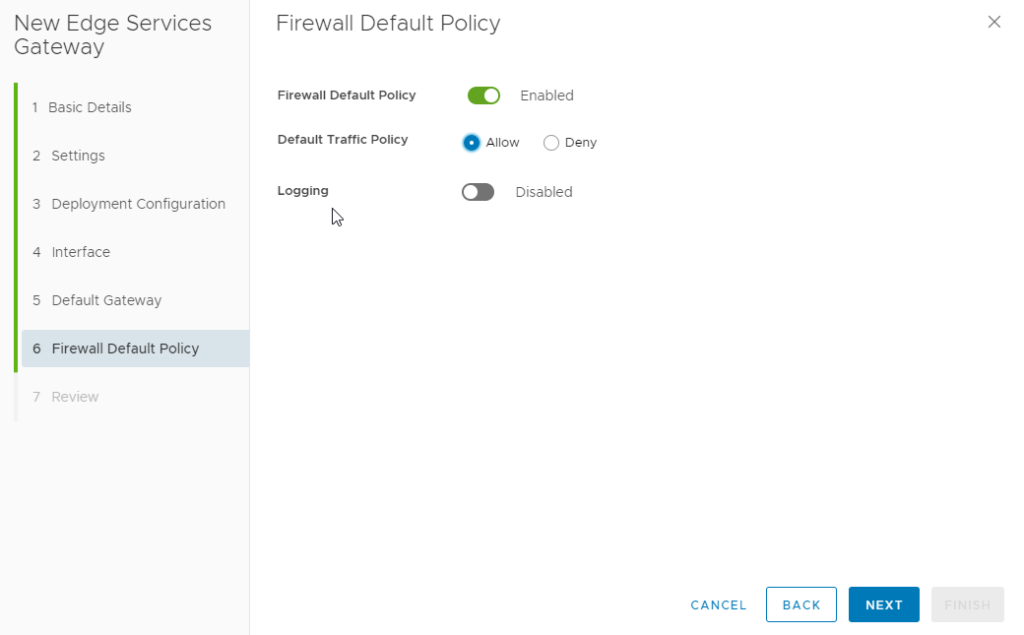
Step 1 : Deploy a NSX Edge
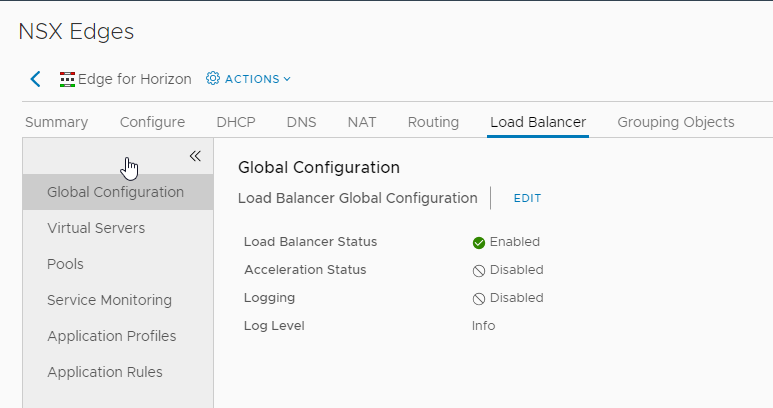
Step 2 : Configure the load balancer
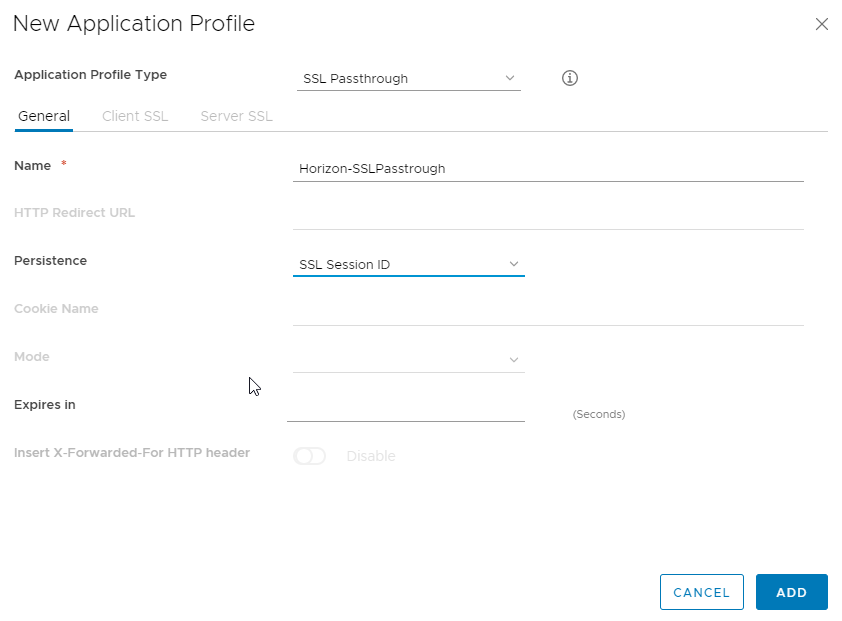
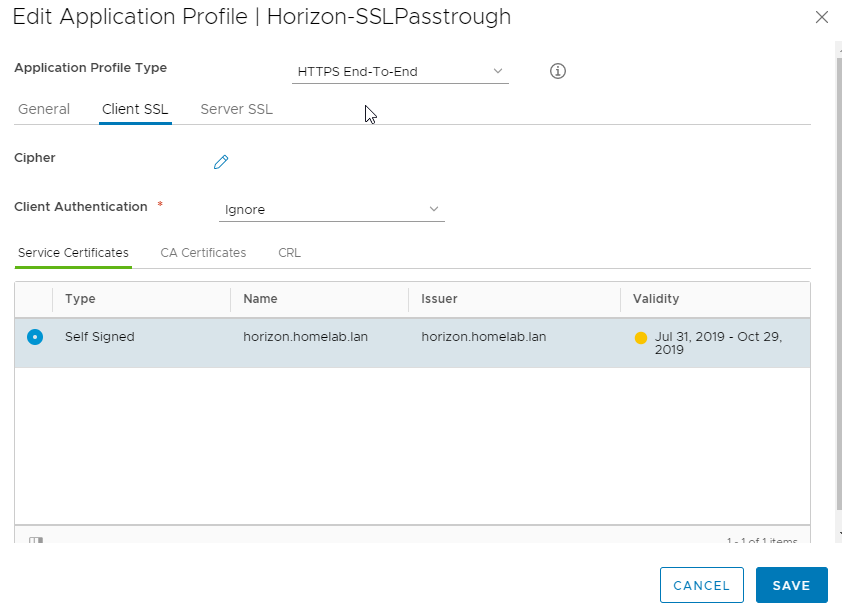
Step 3 : Create an application profile
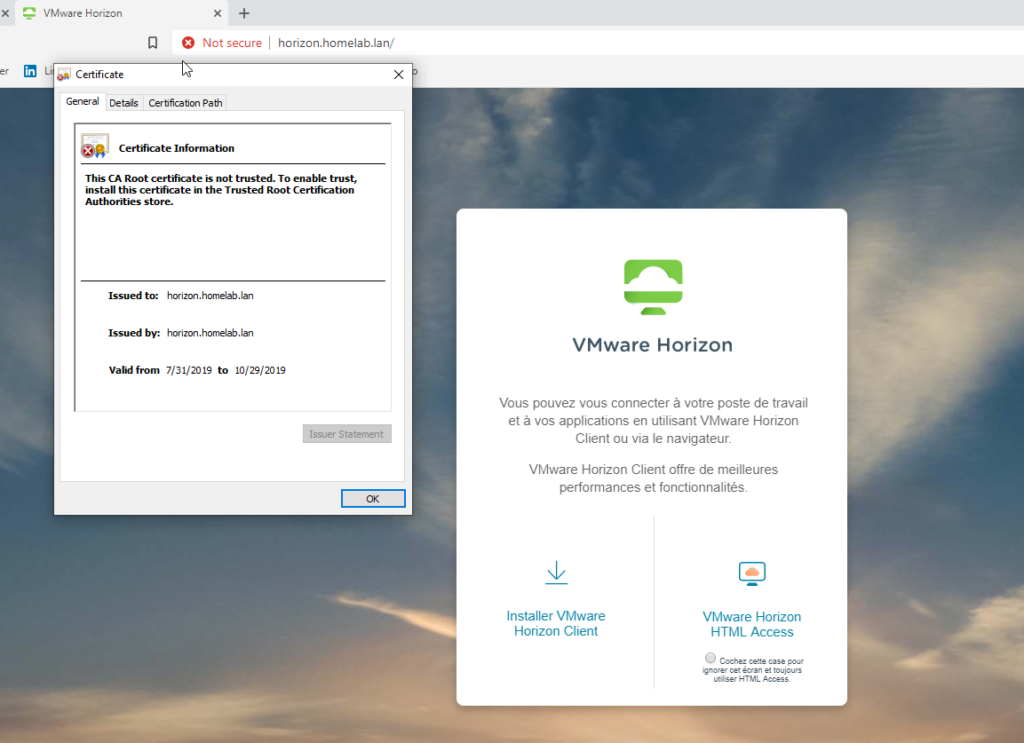
In a first time, i’ll do not use any certificate. Each broker will show its own self signed certificate.
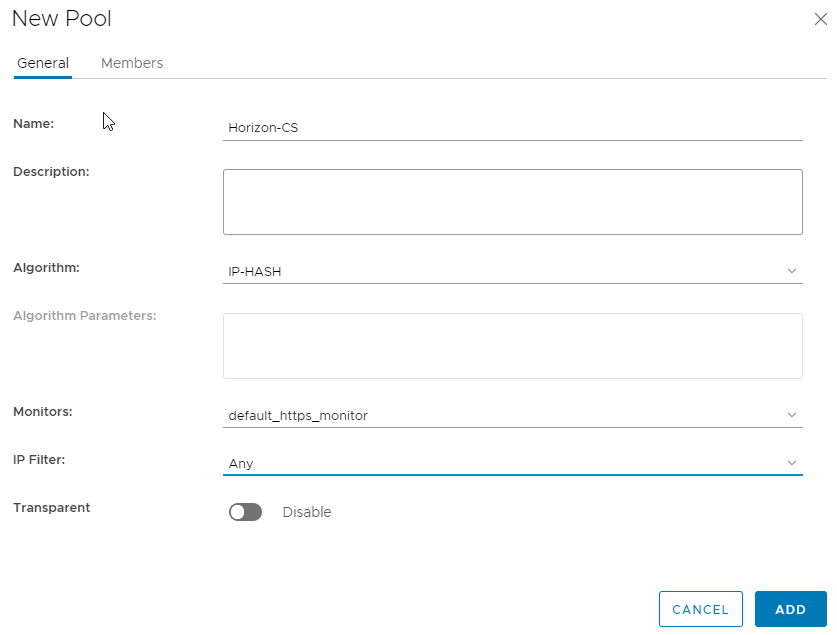
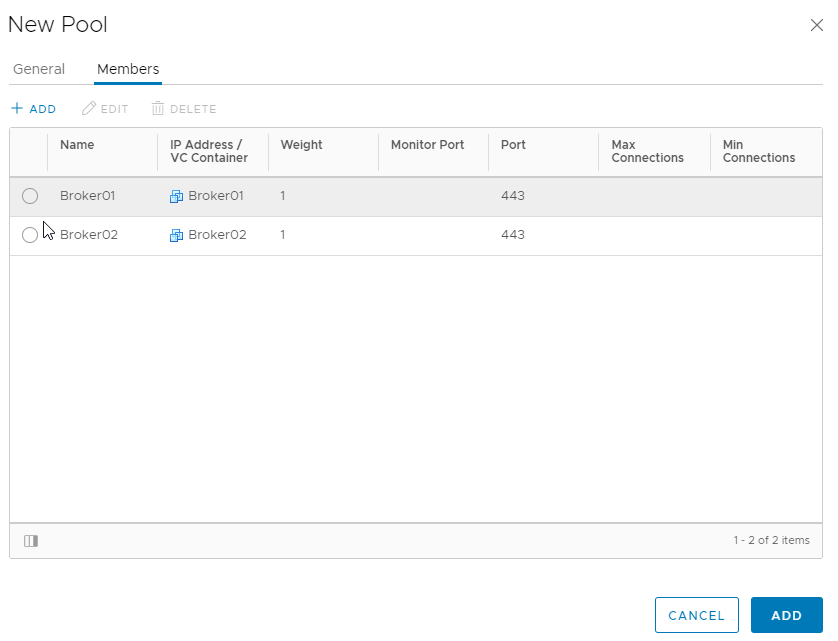
Step 4 : Create a new pool containing my two broker
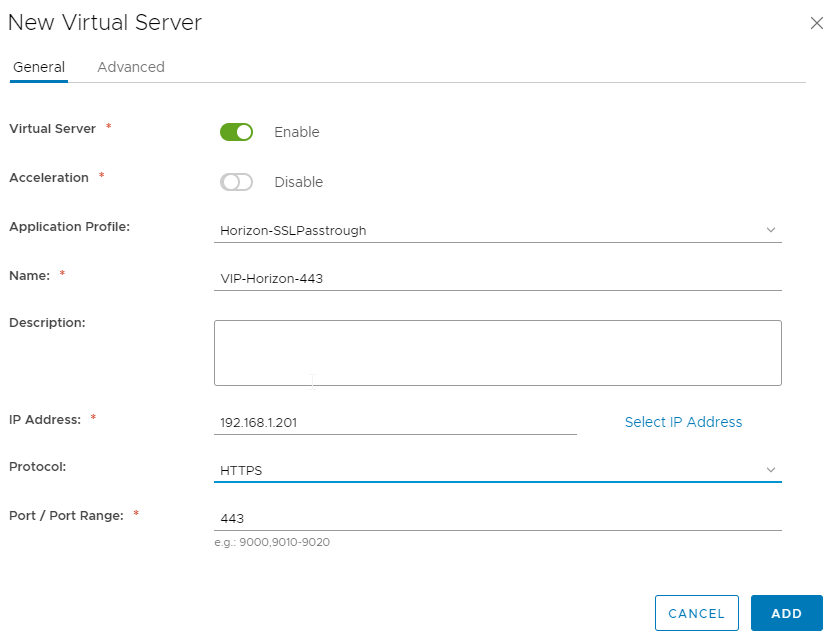
Step 5 : Create a virtual server
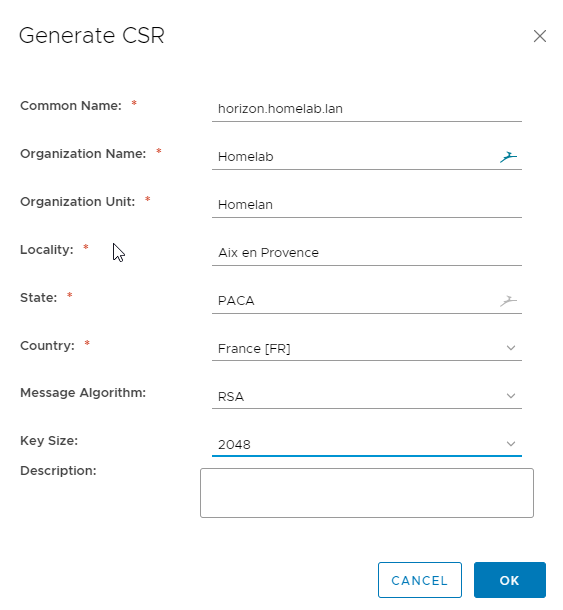
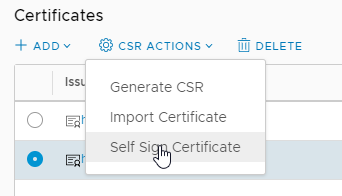
Step 6 optionnal : Add a self signed certificate
Self your self signed certificate on the Client and Server side.